OpenAI's GPT-4o may have survived its first brush with going offline, but it won't be as lucky this time. OpenAI has officially retired GPT-4o, the ChatGPT […]
Software Development and Custom Solutions for Businesses What is Software Development & Custom Solutions? Custom software development involves designing, building, and deploying applications tailored to a […]
Starmer 'appeasing' big tech firms, says online safety campaigner Getty Images A leading campaigner has accused the prime minister of "appeasing" big tech companies and being […]
Trump Mobile is already failing to deliver on some early promises, according to the latest report from The Verge. The report revealed the near-final design of […]
ASUS appears to be shifting its business operations away from smartphones. According to translations of recent quotes from Chairman Jonney Shih, the company does not plan […]
A pro-Russian hacker group has come forward as the perpetrator of a DDoS attack on the French national postal service La Poste that took place on […]
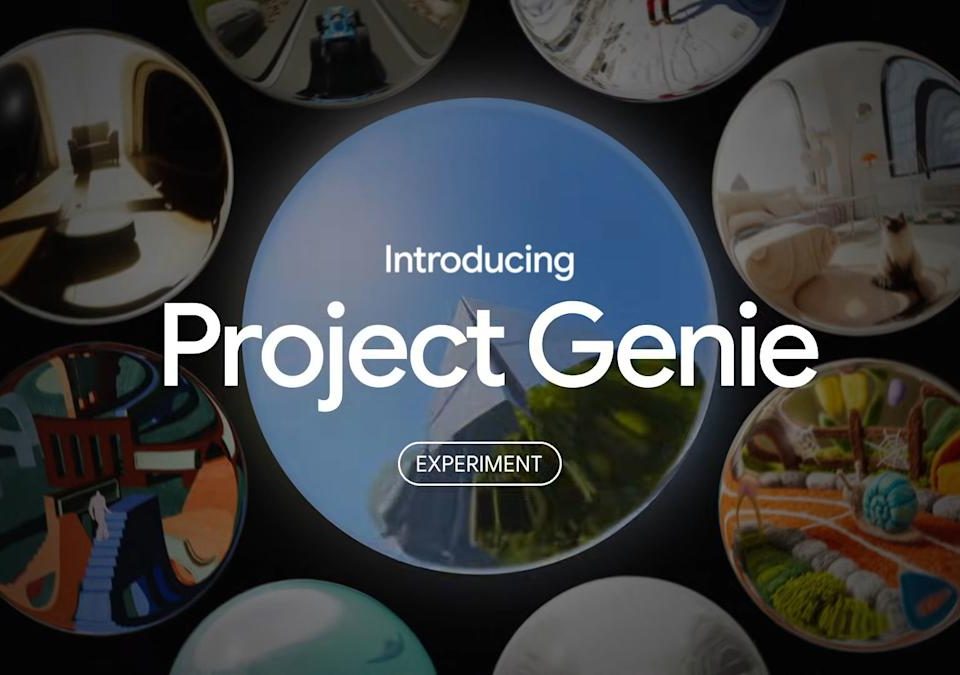
This past summer, Google DeepMind debuted Genie 3. It’s what’s known as a world world, an AI system capable of generating images and reacting as the […]
Back in August, Adobe debuted Acrobat Studio. The new service saw Adobe bring the humble PDF into the 21st century with support for a handful of […]
Sandfall Interactive, the developer of Clair Obscur: Expedition 33, knows how to ride the wave. Right after the visually stunning RPG finished dominating The Game Awards, […]
Porn site fined £800,000 for not rolling out age checks Getty Images Ofcom has fined porn company Kick Online Entertainment SA £800,000 for failing to introduce […]
Google wanted to remove Assistant from most Android phones by the end of 2025 and replace it with Gemini. But now the company has announced that […]
Microsoft has announced some solid additions to Game Pass this month, ranging from AAA titles to indies, including some of our favorites from 2024 and 2025. […]
Ofcom asks X about reports its Grok AI makes sexualised images of children 10 hours agoShareSaveChris Vallance,Senior technology reporter,Laura CressandLiv McMahon,Technology reportersShareSaveNurPhoto via Getty Images Ofcom […]
Smart fridges are a dime a dozen at CES, and LG and Samsung have thoroughly explored what's possible when you connect your fridge to the internet […]
Is AI in recruitment a 'race to the bottom'? 15 hours agoShareSaveMaryLou CostaTechnology ReporterShareSaveThe AI which interviewed MaryLou Costa It's my first job interview in more […]